UPDATE: with the Intune 2303 release, Endpoint security firewall policy now supports logging configurations. see: https://learn.microsoft.com/en-us/mem/intune/fundamentals/whats-new#endpoint-security-firewall-policy-support-for-log-configurations
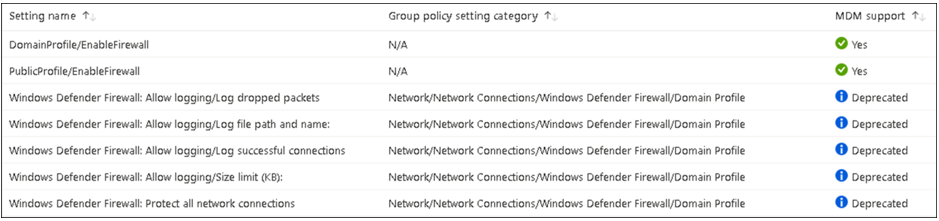
Following are the new settings, all found in the Firewall configuration service provider (CSP):
- Enable Log Success Connections
- Log File Path
- Enable Log Dropped Packets
- Enable Log Ignored Rules
Auditing is an integral part of any security solution. In the case of the firewall, auditing allows to determine if the rules are properly configured, the traffic is allowed/blocked as expected, helps to identify vulnerabilities, or customize the rules to respond to a security issue just to name a few. In this post, I will explain how to enable audit logs for Windows Defender Firewall in Microsoft Intune.
Windows Defender firewall offers the option to log succeeded and dropped connections. This audit log can be enabled per firewall profile (Domain, Private Public) offering good flexibility and granular control to track only the relevant data.
The logging can be managed through different methods, like Group Policy, SCCM, or from the device itself, as shown below:
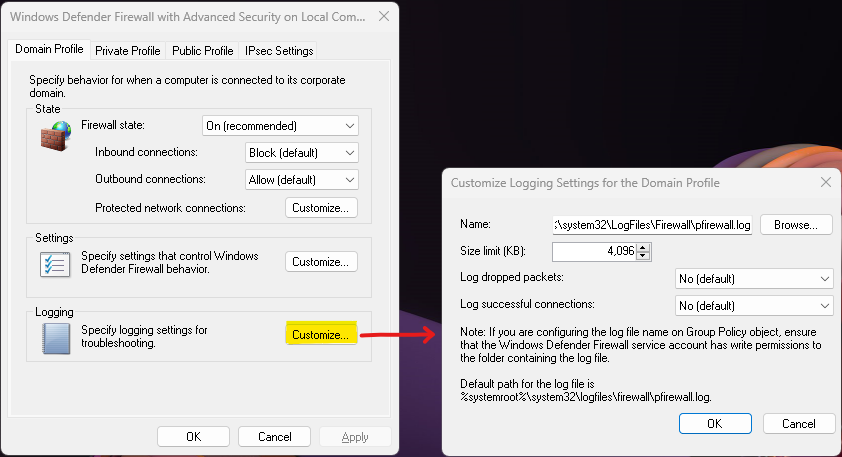
However, this logging option is not available to be managed via Intune. Here the context of this configuration:
Windows exposes its settings to Intune (or any other MDM solution) through Configuration Service Providers, or CSP’s. The Firewall CSP does not offer control over it.
The firewall logging leverages Windows auditing settings. This feature offers better capabilities than writing on a dedicated log, leveraging the robustness the Event viewer service has to offer and can track allowed and dropped connections among others. you can easily check using the Group Policy Analytics. If you attempt to analyzes the logging control from a GPO to Intune, you will see something like this (see my latest update on this article, Firewall CSP now supports TXT logging)
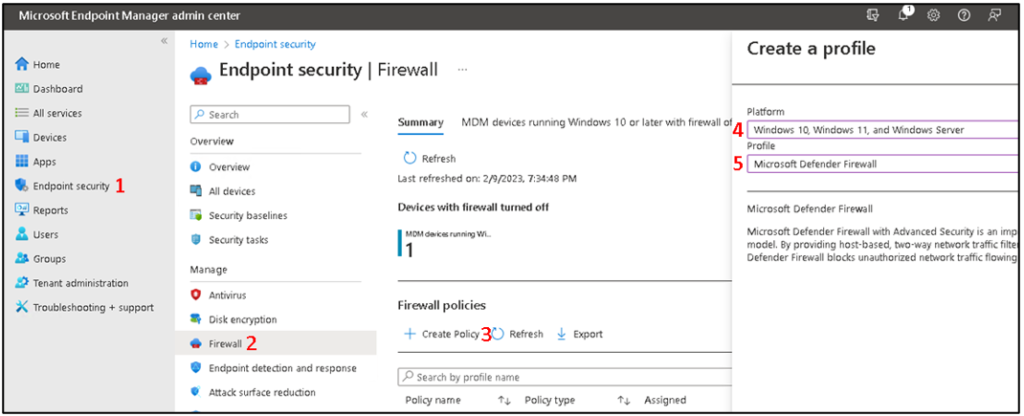
So, how to configure the Defender firewall audit settings? Go to Intune console -> Endpoint Security (1) -> Firewall (2) -> Create a Policy (3) for Windows 10, Windows 11 and Windows Server (4) and select: Microsoft Defender Firewall (5). Then create.
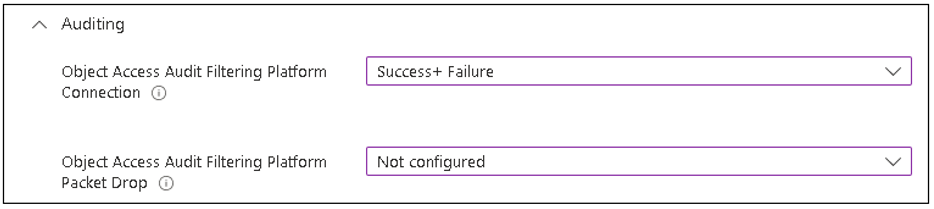
Configure the policy name and then set the configuration settings you need for your firewall profile. The Audit options are available at the end of the list of settings to configure.
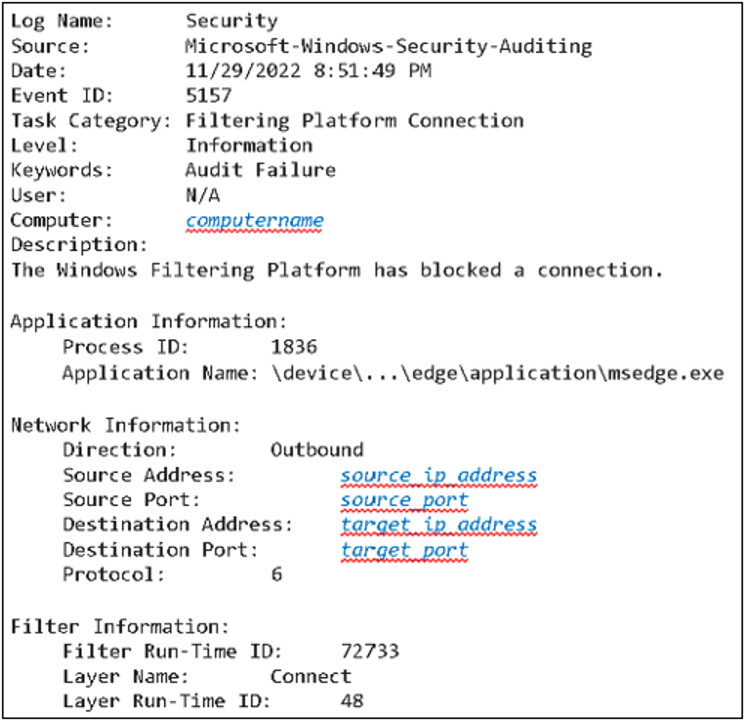
Object Access Audit Filtering Platform Connection: This setting audit connections that are allowed or blocked by the Windows Filtering Platform (WFP). If the setting is configured to “Success+ Failure” this will track allowed (event id: 5156) and blocked connections (event id: 5157)
Object Access Audit Filtering Platform Packet Drop: Events 5152 and 5153 are logged. these event logs all the particulars about a blocked packet including the filter that caused the block. However, there is not, at least for me, reason to use this option as the same data is provided by “Object Access Audit Filtering Platform Connection”.
If the requirement is to track allowed and blocked connections, then set the configuration as follow:
The events created are logged under the Event Viewer -> Security node of the computer receiving the firewall policy. For example, a block operation of Edge app trying to access a website.
Pro tips…
Why is the Auding included in the Firewall configuration, but it is not part of the Firewall CSP?
The Firewall configuration blade contains information from different CSP’s, Firewall CSP for firewall settings and Audit Object Access for auditing settings. Audit Policy CSP – Windows Client Management | Microsoft Learn
The firewall logging was enabled through Intune; however, legacy logging seems to be still working.
This may happen if the legacy method for logging was enabled. As Intune does not control it, it does not do anything about it. When an action occurs, (an allowed or blocked connection) Firewall service will log the entry on both locations, the event viewer, and the txt log. If the customer does not want it, they have to disable it from the endpoint itself, through GPO or a PS script deployed from Intune.
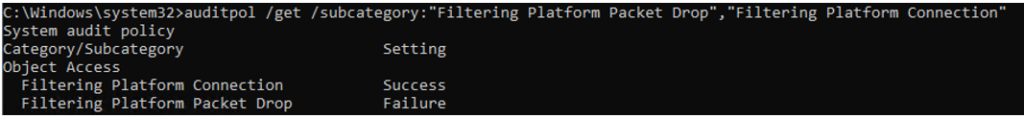
How to determine if audit logging is enabled on a device? From an elevated command prompt, run: auditpol /get /subcategory:”Filtering Platform Packet Drop “,”Filtering Platform Connection”.
Do you know any other method to control the Defender firewall audit logs through Microsoft Intune? Please leave your comments below.
